A fundamental reason for Mekorma Payment Hub is its security features. Whether you are processing your payments by check, EFT or outsourcing through Mekorma Enhanced ePayments, security is crucial. Knowing that your workflow is protected is what can give you peace of mind when you print checks with automatic signatures or send payments out through your outsource provider or bank. It is a way of insuring that the proper controls are in place for separation of duties and oversight, essential for fraud prevention.
With Mekorma Payment Hub, the same set of security rules apply whether you are processing checks in-house, creating EFT files to send to the bank or automating your payments completely with Mekorma Enhanced ePayments.
Mekorma Task-Based Security
As needs have grown, so has the security model which is rich with capabilities. Our security model is called Task-Based Security, which was introduced in Mekorma Payment Hub bx76. The fundamentals are covered:
- Signature logic with encryption .
- Dollar-value ranges, a.k.a., Threshold levels, for designing your security rules.
- The Approval Workflow Notification System lets approvers know by email or text when they need to approve.
- Automatic batch splitting allows payments that are fully approved to go out without waiting for other payments.
- Approval rules can be configured not only by dollar-value but also by Vendor Classes
In addition, Mekorma security has been enhanced with the following, all driven by user request:
- You can break your dollar value groupings down as finely as you want for total control. No limit on the number of levels.
- You can assign any number of approvers to a dollar value group/threshold level.
- Any one approver can be assigned to as many dollar value groups as you need.
- The Mobile approval system option, Power Approvals, built from Microsoft Power Platform, lets approvers approve on the go.
- Whole payments or even individual vouchers can be rejected when approving.
- Out-of-Office notification and approval delegation can be configured.
Thinking through what you want to do is an important part of implementing a fully functional approval system and this guide will help you.
Mekorma Legacy Security
Mekorma is fiercely committed to our existing users, so we have continued to maintain our older security models, which we call Legacy Security. This is what Mekorma users have employed for builds previous to x76 and includes security by:
- User ID
- Checkbook ID
- Default GP security
Because Mekorma is fiercely committed to ensuring your payment process is as secure as possible, we continue to develop features and improvements for our Task-Based Security model. However, Mekorma Legacy Security (checkbook / user based) models will be deprecated as of build x84. Moving forward, if your security is configured by checkbook or User ID, you can continue to use it but as of the March 2022 Payment Hub release, the functionality will no longer be supported. Please continue to watch our newsletters and website for updates and announcements.
To understand the benefits of Task-Based security, please see this detailed list of features by security model and how they compare. Our Customer Success team is happy to help with the transition and implementation to our Task-Based Security model so you can continue to enjoy the peace of mind that comes with more robust security to your payments.
What is the Default Setting and What Happens When I Upgrade?
Task-Based security is the default setting. However, please be assured, if you are an existing customer using Legacy Security, the Mekorma upgrade process honors your Legacy Security settings and you have time to plan when you want to implement the new security system.
Selecting a Security Model
Mekorma lets users decide which security model to use, and you can readily switch between Task-Based Security and Legacy Security.
For those that use Legacy Security, there are scenarios in which you may need to reenable Legacy Security. For example, if you upgrade to a newer Mekorma build, any new company you add will, by default, have its security model set to Task-Based Security. You will need to set the security model to Legacy Security for these new companies. All existing companies under Legacy Security will remain with that security model in place.
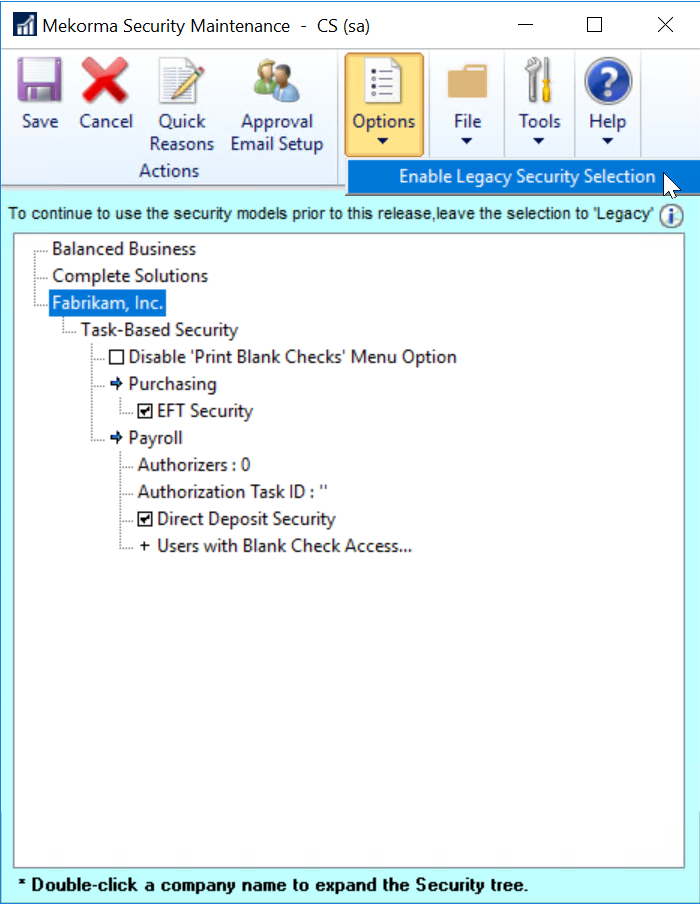
To select the security model you want to use, access the Security Setup window (Mekorma Area Page > Setup > System > Security Setup).
- In the Security Setup window, double-click on the company you would like to configure. This will expand the list of options.
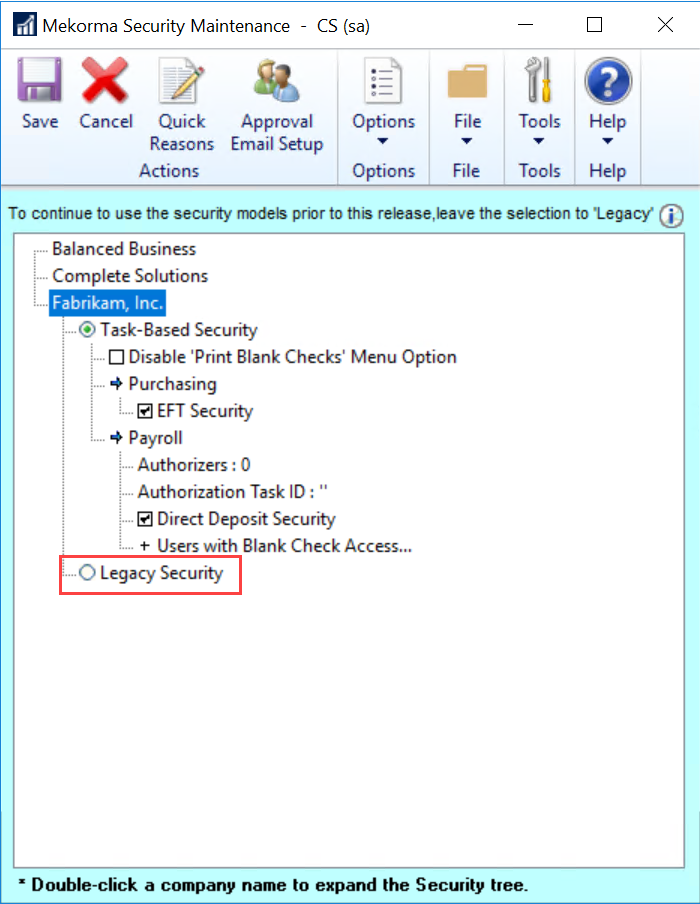
- Task-Based Security is selected by default with new builds. Enable Legacy Security by clicking on the corresponding radio button.
- If Legacy Security is selected, clicking on the Legacy Security hyperlink will open the security configuration window, allowing you to set passwords by user ID, Checkbook, or Standard GP Security (‘None’).
- If Task-Based Security is chosen, clicking on the Task-Based Security hyperlink will take you to the Threshold Maintenance window, where you can configure the Threshold IDs that will later be applied to checkbooks.
- Selecting Legacy Security will warn you that this is a ‘no passwords’ security model. Click OK to continue.
- Click Save. When switching security models, you must log out of Dynamics GP, then log back in for the changes to take effect.
Need more help with this?
We value your input. Let us know which features you want to see in our products.